PGP Overview
PGP( Pretty Good Privacy ) is a commonly used method to protect files delivered from a source to a target.
The following diagram reviews the main steps in the process.
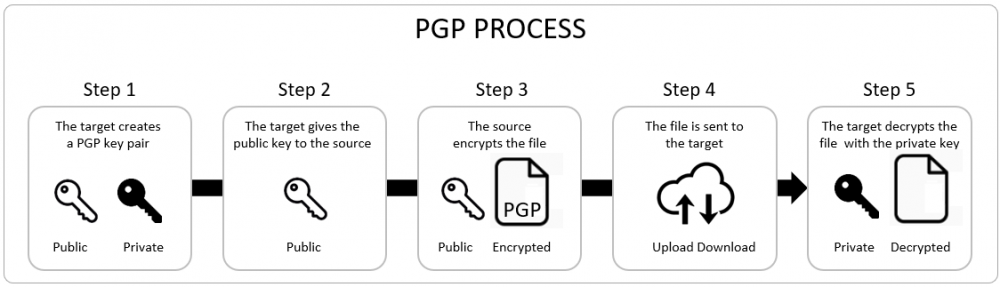
You can implement PGP protection end-to-end using Thru, but you can also use your existing key generation and encryption/decryption tools and use Thru only for file delivery.
PGP is implemented for the following transport types.
• Many-to-One with No Flow Tool – It covers the scenario where partners are sending files to the enterprise.
• Private delivery over One-to-Many with no Flow tool – It covers the scenario where the enterprise needs to send protected files to one or more external parties like suppliers.
The steps to configure each scenario are simple.
The following sections will walk you through it.
Note : Thru only stores public keys, so files can never be compromised by breaking into the system.
Thru can also act as PGP public key directory
The directory can never be breached because Thru does not store PGP private keys at all.
When it generates a key pair it gives you the private and then deletes it.
Public keys are only shown to organizations which need to use them, only within a transport.
The Transport client has no settings for a Public Key because the encryption side (on push) is completely transparent.
The Transport client uses the target organization (-o parameter) and the transport code to make an API call which returns the public key it needs to use.
The user does not need to define the key – the client will always use the right one.
